Bridging Public Clouds with CloudRouter
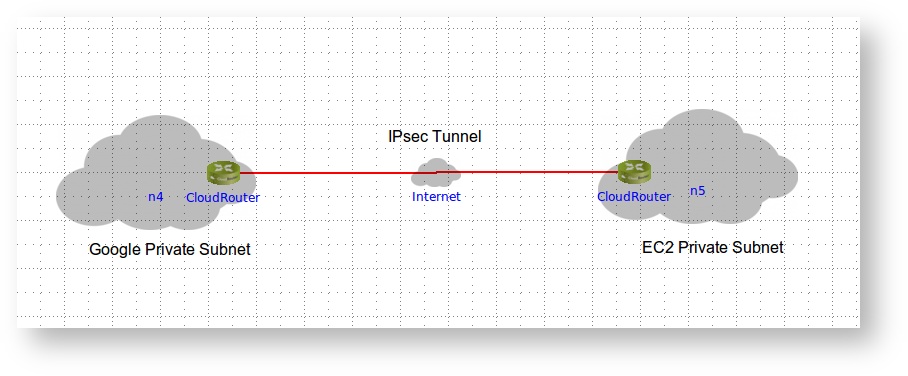
The goal of this article is to showcase how to utilize CloudRouter to setup a secure Virtual Private Network (VPN) IPsec tunnel between two public clouds environments one in AWS EC2 and one in Google Cloud.
Topology
Setup in AWS EC2
Launch CloudRouter
Find the CloudRouter image and launch it in AWS EC2. Instructions to launch are here - http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/launching-instance.html
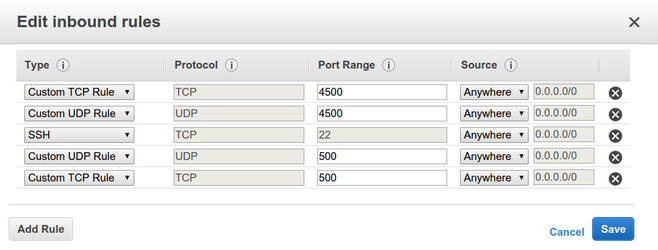
Edit Firewall Rules
We have to allow traffic on ports 500 and 4500 for the ipsec tunnel.
Installing libreswan
yum -y install libreswan
Editing /etc/ipsec.conf
## general configuration parameters ##
config setup
plutodebug=all
plutostderrlog=/var/log/pluto.log
protostack=netkey
nat_traversal=yes
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/16
## disable opportunistic encryption ##
oe=off
## connection definition ##
conn demo-connection
authby=secret
auto=start
ike=3des-md5
## phase 1 ##
keyexchange=ike
## phase 2 ##
phase2=esp
phase2alg=3des-md5
compress=no
pfs=yes
type=tunnel
left=172.31.13.92 ## EC2 internal IP Address
leftsourceip=52.8.28.128 ## EC2 external IP Address
leftsubnet=172.31.0.0/16 ## EC2 Internal subnet/mask
leftnexthop=%defaultroute
right=104.199.167.94 ## Google Cloud External IP Address
rightsubnet=10.240.0.0/16 ## Google Cloud Internal Subnet/mask
rightsourceip=10.240.155.115 ## Google Cloud Internal IP Address
forceencaps=yes
Editing /etc/ipsec.secrets
52.8.28.128 %any : PSK "this is my pre shared key" 172.31.13.92 %any : PSK "this is my pre shared key" include /etc/ipsec.d/*.secrets
Start ipsec daemon
# systemctl start ipsec
Setup in Google Cloud
Launching CloudRouter
Find the raw image of CloudRouter provided here - https://cloudrouter.org/getting-started/ and launch it on Google Cloud. Instructions to import your image to Google Cloud are located here - https://cloud.google.com/compute/docs/images#import_an_image
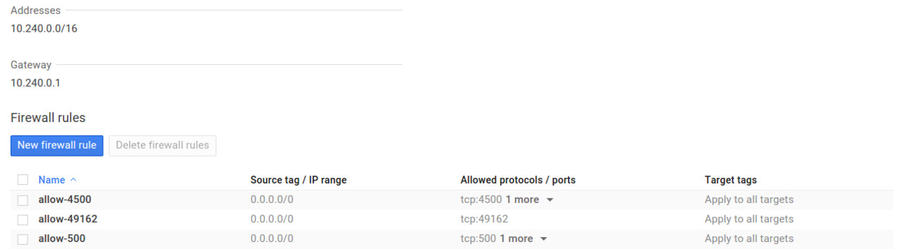
Edit Firewall Rules
We have to open up traffic on ports 500 and 4500 for IPsec tunnel.
Editing /etc/ipsec.conf
## general configuration parameters ##
config setup
plutodebug=all
plutostderrlog=/var/log/pluto.log
protostack=netkey
nat_traversal=yes
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/16
## disable opportunistic encryption ##
oe=off
## connection definition ##
conn demo-connection
authby=secret
auto=start
ike=3des-md5
## phase 1 ##
keyexchange=ike
## phase 2 ##
phase2=esp
phase2alg=3des-md5
compress=no
pfs=yes
type=tunnel
left=10.240.155.115 ## Internal Google IP address
leftid=104.199.167.94 ## External Google IP address
leftsubnet=10.240.0.0/16 ## Internal Google Subnet/mask
leftnexthop=%defaultroute
right=52.8.28.128 ## External EC2 IP Address
rightsubnet=172.31.0.0/20 ## Internal EC2 Subnet/mask
rightid=172.31.13.92 ## Internal EC2 IP address
forceencaps=yes
Editing /etc/ipsec.secrets
104.199.167.94 %any : PSK "this is my pre shared key" 10.240.155.115 %any : PSK "this is my pre shared key" include /etc/ipsec.d/*.secrets
Start ipsec daemon
# systemctl start ipsec
Test Connectivity between AWS EC2 and Google Cloud
Check Status of IPsec Tunnel
[root@ip-172-31-13-92 ~]# grep -i established /var/log/pluto.log
"demo-connection" #1: STATE_MAIN_I4: ISAKMP SA established {auth=PRESHARED_KEY cipher=oakley_3des_cbc_192 integ=md5 group=MODP2048}
"demo-connection" #2: STATE_QUICK_I2: sent QI2, IPsec SA established tunnel mode {ESP/NAT=>0x3d420cd3 <0x94844801 xfrm=3DES_0-HMAC_MD5 NATOA=none NATD=104.199.167.94:4500 DPD=passive}
"demo-connection" #3: STATE_MAIN_R3: sent MR3, ISAKMP SA established {auth=PRESHARED_KEY cipher=oakley_3des_cbc_192 integ=md5 group=MODP2048}
"demo-connection" #4: STATE_QUICK_R2: IPsec SA established tunnel mode {ESP/NAT=>0x9ed968b4 <0xa0c6cbbc xfrm=3DES_0-HMAC_MD5 NATOA=none NATD=104.199.167.94:4500 DPD=passive}
"demo-connection" #5: STATE_MAIN_R3: sent MR3, ISAKMP SA established {auth=PRESHARED_KEY cipher=oakley_3des_cbc_192 integ=md5 group=MODP2048}
Check availability of routes
[root@ip-172-31-13-92 ~]# route -n Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 0.0.0.0 172.31.0.1 0.0.0.0 UG 0 0 0 eth0 10.240.0.0 172.31.0.1 255.255.0.0 UG 0 0 0 eth0 172.31.0.0 0.0.0.0 255.255.240.0 U 0 0 0 eth0
Ping Test from EC2 to Google Cloud
[root@ip-172-31-13-92 log]# ping 10.240.155.115 PING 10.240.155.115 (10.240.155.115) 56(84) bytes of data. 64 bytes from 10.240.155.115: icmp_seq=1 ttl=64 time=273 ms 64 bytes from 10.240.155.115: icmp_seq=2 ttl=64 time=272 ms 64 bytes from 10.240.155.115: icmp_seq=3 ttl=64 time=272 ms ^C --- 10.240.155.115 ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 2002ms rtt min/avg/max/mdev = 272.920/273.111/273.455/0.243 ms